Build3rs Stack: Nym

Welcome back to the Build3rs Stack, Fleek’s web3 infra overview series! This week dive into Nym– the privacy platform protecting end users’ communication patterns, IP addresses, and metadata.
Developers can use Nym to create privacy-enhanced applications (PEAs), using an architecture of Nym nodes, clients, and Nym’s blockchain, Nyx.
Let’s get into how you can leverage Nym in your Web3 builds:
TLDR; What is NYM?

Nym provides network-level privacy-preserving software for end users and developers. Along with protection against sophisticated end-to-end attackers, Nym also solves a major problem facing developers today: traffic patterns are visible to anyone observing or monitoring a network. Nym solves this, routing traffic through a decentralized mixnet.
Key Aspects of Nym:
- Decentralized: Operated by a community of node operators and stakers.
- Tokenized: Incorporates incentivization to reward operators.
- Open Source: All Nym software is open source and can be audited by anyone.
- Permissionless: Anyone can build with Nym, or spin up their own Nym node.
- Trustless: The mixnet is trustless, meaning neither the operator nor the system can access users’ private information.
How Does Nym Work?
At its core, Nym employs blinded, re-randomized, decentralized credentials to transport data. This protects privacy at the network level, by encrypting and relaying internet traffic through a multi-layered mixnet network. Within each layer, mix nodes combine and mix a user’s internet traffic with other network users.
Nym and its privacy-enhancing signature scheme, called Coconut, creates a paradigm shift in how we approach private resource control and access: moving from an identity-based system centered around who you are, to a privacy-preserving right to use system.
Nym Traffic Flow
- Mixnet breaks Sphinx packets into uniformly sized packages and encrypts them according to the path it will take.
- Mixnet re-orders and sends broken packets through various gateways and mix nodes.
- Packets are sent through the mixnet with a combination of real and fake, dummy traffic.
- Each time a packet is sent from one node to another, each known as a
hop, a layer of decryption is removed from each packet– this reveals the address of the next hop. - The packet is held in each layer by a node for a variable amount of time, before being forwarded to the next one.
- When each hop is completed, the receiving node sends back an acknowledgment (ack), so the sending node knows it was received.
The traffic follows a similar pattern every time–first being sent by the client registered gateway, through a mix node on three different layers on the network, and finally to the recipient’s gateway or application client.
Nym in Features: Zk-nym, NymConnect, Mixnet
Zk-nym
Zk-nym’s are credentials that can be used to access digital apps and services without revealing the end user’s sensitive information. Based on the Coconut protocol, they allow users to request anonymous credentials from issuing authorities, like validators from Nym’s Cosmos-based blockchain (Nyx).
These validators issue anonymous credentials that have “threshold issuance,” meaning they only hold part of the key of the credential and cannot piece together the full key to deanonymize end users. This makes the ability to cryptographically prove sensitive information to a digital service, while still maintaining privacy, possible.
NymConnect
NymConnect acts as a versatile interface for connecting to applications in the Nym Mixnet. The coolest thing about NymConnect is that it can enhance the privacy for any app that can run SOCKS5, including Telegram, Electrum, and Blockstream Green.
Mixnet
The aforementioned mixnet is the backbone of Nym, encrypting and mixing sphinx packet traffic, protecting communication patterns and traffic from external parties. Based on a modified Loopix Anonymity System, it is comprised of:
The Mixnet is crucial for the flow of anonymous traffic within the network, making it a fundamental component of the Nym platform.
Applied Use-Cases
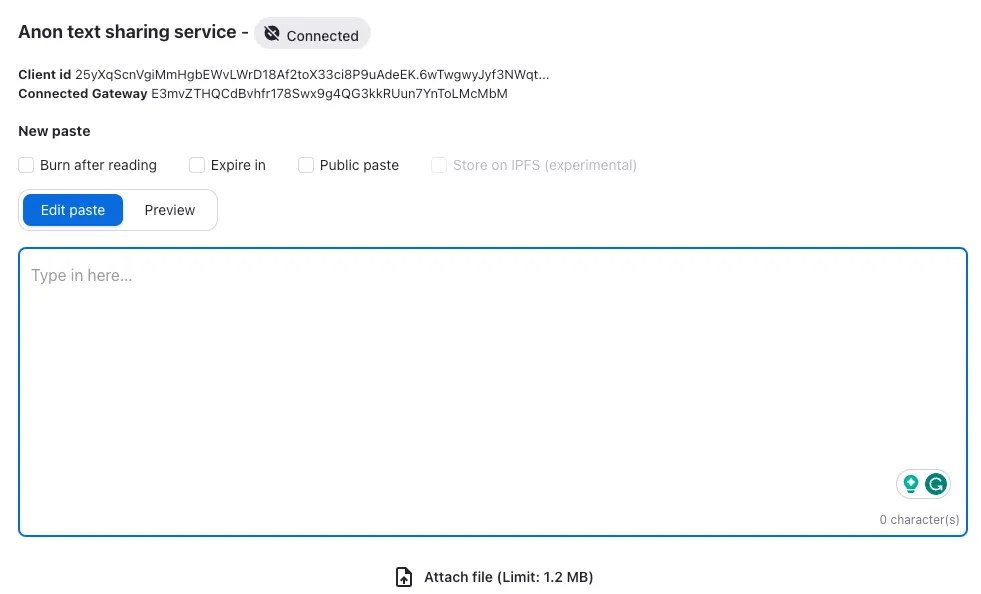
A great example of building with Nym is Pastenym– an anonymous messaging service, that allows users to send end-to-end encrypted texts wallet-to-wallet. Users can choose to have the message burnt after reading, expire after a set amount of time, have it stored on IPFS, or have it not encrypted at all.
Anonymous e-cash payments or self-sovereign identities are also possible with Nym, using a zk-nym scheme to enable private financial transactions or prove you’re a certain age without revealing your birthdate/personal information.
Getting Started With Nym
- Developer Portal
- Quickstart Guide
- Rust SDK
- TypeScript
- MixNode Starting Guide
- NymConnect
- Nym Wallet
- Nym vs other Systems
- Blog
That’s all for this week on Nym! This blog should be a good jumping-off point to get started with Nym, giving you all the resources you need to start building your first Privacy-enhanced application.
Follow Nym on X to stay up to date on what the team is working on.
If you enjoyed learning about the protocol check out more of our Build3rs Stack articles.
You can also join our Discord server to jam with the team and learn more!
For more resources, visit our LinkTree⚡